Computer communications and networks refer to the systems and infrastructure that enable communication and data exchange between computers and other devices. This field encompasses a broad range of technologies and protocols that facilitate the transmission of information across different types of networks, including local area networks (LANs), wide area networks (WANs), and the Internet.
Key components of computer communications and networks include:
- Protocols: These are rules and standards that govern how data is transmitted and received over a network. Examples include TCP/IP (Transmission Control Protocol/Internet Protocol), HTTP (Hypertext Transfer Protocol), and Ethernet.
- Networking Hardware: This includes devices such as routers, switches, modems, and network interface cards (NICs), which are used to establish connections and manage data traffic within a network.
- Network Topologies: The physical or logical layout of a network, determining how devices are interconnected. Common topologies include star, bus, ring, and mesh.
- Transmission Media: The physical medium used to transmit data between devices in a network. This can include copper wires, fiber-optic cables, and wireless communication technologies such as radio waves and infrared.
- Network Architectures: The design and structure of a network, including its layers, protocols, and communication models. Common architectures include client-server, peer-to-peer, and hybrid models.
- Network Security: Techniques and mechanisms used to protect data and resources from unauthorized access, manipulation, or destruction. This includes encryption, firewalls, intrusion detection systems, and authentication protocols.
- Network Management: The process of monitoring, configuring, and optimizing network performance and resources. This involves tasks such as network monitoring, troubleshooting, and capacity planning.
- Internet of Things (IoT): The network of interconnected devices and sensors that communicate and exchange data over the internet. IoT technologies enable the automation and integration of various systems, from smart homes and cities to industrial processes and healthcare.
Computer communications and networks play a crucial role in modern society, facilitating communication, collaboration, and the exchange of information across the globe. As technology continues to evolve, new advancements in networking continue to emerge, driving innovations in areas such as cloud computing, virtualization, and mobile networking.
CS402: Computer Communications and Networks Exam Quiz Answers

Question 1: Distributed email was invented in the early 1970s. Before that, which of the following happened?
- Tim Berners-Lee invented the World Wide Web
- Reports by Paul Baran Outlining packet networks were released
- GOPHER was released by researchers at the University of Minnesota
- Marc Andreessen and Eric Bina developed and introduced the Mosaic web browser
Question 2: Would you use a distributed system or a network to allow several computers in your organization to use the same printer? Why?
- A network, because networks are the only way to interconnect different types of hardware
- A network, because users in the organization need to be exposed to all the actual machines, including the printers
- A distributed system, because all printers must operate on top of the middleware that is present in distributed systems
- A distributed system, because that is the best way to prevent end-users from having to deal with the complexities of networks
Question 3: Which of the following statements about the physical layer is true?
- It uses the port number to deliver traffic
- It changes the value of a bit being transmitted due to electromagnetic interference
- It specifies the shared protocols and interface methods used by hosts in a communications network
- It provides the mechanism for opening, closing, and managing a session between end-user application processes
Question 4: Which of the following best describes a Network Request for Comments (RFC)?
- A document published by the IEEE to define protocols such as 802.3/Ethernet
- A document published by vendors to describe the network capabilities of their devices
- A document published by Cisco that is used to develop network protocols using their devices
- A document published by the IETF that defines new networking standards and shares technical information
Question 5: You open a command prompt window on your Windows PC and execute the two commands in bold, which give these two responses from your computer:
c:\Users\saylor_000> ipconfig
Connection-specific DNS suffix: home
Link–local Ipv6 address………..fe08::5d:45da:b569:cba0%10
Ipv4 Address………………….192.168.1.5
Subnet Mask…………………..255.255.255.0
Default Gateway……………….192.168.1.1
c:\Users\saylor_000> arp -a
Internet Address Physical Address Type
192.168.1.1 16–1b-eb-76–42–9b dynamic
192.168.1.7 7c–2b–33–6a–42–55 dynamic
255.255.255.255 ff-ff-ff-ff-ff-ff static
You follow that by issuing the following command:
c:\Users\saylor_000> ping 172.217.10.238
In response, which of the following will the system issue?
- A DNS message requesting the common name for 172.217.10.238
- A DHCP message with an L3 destination address of 172.217.10.238
- An ARP message requesting the physical address of 172.217.10.238
- An ICMP message with an L2 destination address of 16-1b-eb-76-42-9b
Question 6: Which of the following is one of the main differences between OSPF and RIP?
- OSPF sends update packets every 30 seconds, while RIP only sends update packets when a topology change is detected
- OSPF is slower to converge since it has a hop count limit of 100, while RIP is much faster since its hop count limit is only 50
- RIP solves the count-to-infinity problem using a simple Split Horizon algorithm, while OSPF uses Split Horizon with Poison Reverse
- An OSPF router floods updates through all the network, while a RIP router only exchanges updates with connected routers
Question 7: Host H1 sends a packet to Router R1. The routing table in Router R1 sends the packet to Router R2, which is directly connected to Host H1. Which of the following ICMP messages could Router R1 send to H1 to make the system more effective?
- Type 5, Redirect Message
- Type 9, Router Advertisement
- Type 10, Router Solicitation
- Type 15, Information Request
Question 8: A channel with a bit rate of 8 Kbps and a one-way propagation delay of 20 msec is using a go-back-n sliding window protocol with 40-bit frames. What is the send window size (buffer) needed to attain a 100% utilization in an error free environment?
- 40 bits
- 160 bits
- 320 bits
- 640 bits
Question 9: Suppose you have the following characters: A is 01000001, B is 11110000, Flag is 00111100, and Esc is 11110000. You want to transmit the sequence A Esc Flag B. What would the actual bit sequence that you would transmit be if you use the character count technique?
- 00000100 01000001 11110000 00111100 11110000
- 00111100 01000001 11110000 00111100 11110000 00111100
- 11110000 01000001 11110000 00111100 11110000 11110000
- 00111100 01000001 11110000 11110000 11110000 00111100 11110000 00111100
Question 10: What is the main difference between CSMA and CSMA/CD?
- CSMA waits to receive a token before sending data, while CSMA/CD sends data as soon as no collision has been detected.
- CSMA sends data as soon as the media is free, while CSMA/CD will send a token to the destination host in order to preserve the media
- With CSMA, a station will always finish transmitting all of its data, while CSMA/CD stops as soon as collision is detected and retransmits at a random time
- CSMA will start a random timer before retransmission after a collision, while CSMA/CD will retract and start monitoring the media until it becomes available again
Question 11: Three computers are connected to an L2 switch and a repeater in a VLAN-unaware network, as shown in this image. PC A attaches to port 1 of the switch and has a MAC address of aa-ab-ac-11-12-13. PC B attaches to port 2 of the switch and has a MAC address of bb-bc-bd-11-12-13. PC C attaches to port 4 of the repeater and has a MAC address of cc-cd-ce-11-12-13. PC D attaches to port 5 of the repeater and has MAC address dd-de-da-11-12-13.

The switch has this Forwarding Database:
| Address | Port |
| aa-ab-ac-11-12-13 cc-cd-ce-11-12-13 | 1 3 |
PC A sends a frame with a destination MAC address of bb-bc-bd-11-12-13. What will happen in this situation?
- The frame floods ports 2 and 3 in the switch and ports 4 and 5 of the repeater
- The switch sends ARP for MAC bb-bc-bd-11-12-13 before forwarding the frame.
- The switch drops frame, as there is no entry in the FDB for MAC bb-bc-bd-11-12-12
- The switch saves the frame in a buffer until an entry for that address appears in the FDB
Question 12: Use this figure for reference. It indicates the path cost, “PC”, for each LAN.
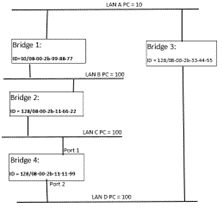
After the STP stabilizes, which of the following will be selected as the root bridge?
- Bridge 1
- Bridge 2
- Bridge 3
- Bridge 4
Question 13: Two transmission methods for wireless systems are the Direct Sequence Spread Spectrum (DSSS) and the Frequency Hopping Spread Spectrum (FHSS). For which of the following you would recommend using DSSS?
- For an environment that is entirely indoors
- When cost is a factor, since DSSS is cheaper
- When short synchronization times are needed
- For an environment with high narrow band noise
Question 14: What protocols are necessary to communicate via VoIP?
- TCP to initiate a call and RTCP to control the transfer of audio and video
- ICMP to ensure that the communication path is present and TCP as the transport for the IP traffic
- RIP to find the path from IP source to destination [and x to do y]
- SIP to initiate a call and RTP to provide end-to-end network transport of audio and video
Question 15: When encrypting data, symmetric encryption is faster and easier to implement. However, key management can become a problem in symmetric encryption systems, since securely getting a new key to both sides can be a challenge. Which of the following might be a way to solve this problem?
- Use a Diffie-Hellman key exchange scheme for the private key
- Use a long period for allowing key changes, to be sure that both parties have ample time
- Switch to asymmetric encryption and use a public key to encrypt and a private key to decrypt
- Increase the length of the encryption and decryption keys in the DES standard from 64-bit to 128-bit
Question 16: You have been asked to install and configure a VPN for a small office that uses a combination of Windows and Linux systems. Which of the following would be your first choice?
- A PPTP-based system
- An L2TP-based system
- An SSTP-based system
- An OpenVPN-based system
Question 17: Establishing a connection to a remote system requires a good, robust solution. In modern networks, RADIUS and TACACS+ provide such solutions. What is one of the main differences between RADIUS and TACACS+?
- RADIUS runs on top of TCP, while TACACS+ runs on top of UDP
- RADIUS does not support protocols like ARA, NetBios, and NASI, while TACACS+ supports all of them
- RADIUS addresses the authentication and authorization issues but lacks accounting, while TACACS+ addresses all of them
- RADIUS encrypts only the password in the access request, while TACACS+ encrypts the whole body of the packet except for the header
Question 18: Two common protocols used to provide router redundancy and achieve high network availability are HSRP and VRRP. For which of the following cases would you decide to use HSRP?
- When you need to support load balancing
- When your network uses only Cisco routers
- When your network uses multiple router vendors, like Cisco and Juniper
- When you need to save address space and receive only one IP address for your virtual router
Question 19: Which of the following types of cable would be most appropriate for a public network?
- Coaxial
- Plenum
- Optical fiber
- Twisted pair
Question 20: Which layer from the OSI layer model facilitates the creation, sending, and receiving of bits?
- Session
- Transport
- Data link
- Physical
Question 21: Which of the following protocols does FTP run on?
- SIP
- SMTP
- TCP
- UDP
Question 22: What is the basic difference between SMTP and IMAP?
- SMTP is a UDP-based protocol, while IMAP is a TCP-based protocol
- SMTP provides support for images in messages, while IMAP is a text-based protocol
- SMTP is a network management protocol, while IMAP is used to send and retrieve email messages
- SMTP could be used to send and retrieve emails, while IMAP is only used to retrieve email messages
Question 23: Which of the following is a difference between HTTP and HTML?
- HTTP normally runs on top of UDP, while HTML runs on TCP
- HTTP is the same as HTML, but works on IPv6 instead of IPv4
- HTTP posts and retrieves web pages, while HTML is a language used to define elements of web pages
- HTTP is a scripting language used to display web pages in a browser, while HTML is the protocol used to secure an HTTP connection
Question 24: In which of the following situations would you want to use FTP instead of TFTP?
- When you need to be able to authenticate users
- When you need to use bootstrap protocols such as BOOTP
- When you need to use initialization protocols such as DHCP
- When you need to use a protocol such as ICMP to troubleshoot a network connection
Question 25: In which of the following scenarios would you choose a peer-to-peer network model over a client-server network model?
- In a school network where sensitive information needs to be protected
- In a content delivery organization that is expected to grow rapidly in the coming months
- In an engineering firm where, multiple users will share a central computer running company-specific software
- In a bank environment with a great amount of users that will be accessing the network via their personal devices
Question 26: Which of the following methods does SSH use to securely transmit data?
- By sending data through an encrypted TLS tunnel
- Authenticating end users and encrypting the data sent between them
- Using public/private asymmetric key pairs to encrypt the whole connection
- Using a single “Well-Known Key” that is paired with all data sent through the network
Question 27: As a network engineer, you need to write a simple socket program. Which of the following parameters will you need to specify when creating a socket?
- Socket type and address format
- Socket address and socket family
- Socket message and socket header
- Socket stream and datagram socket
Question 28: As compared to TCP, which of the following is true of UDP?
- UDP is more reliable
- UDP supports flow control
- UDP has a higher overhead
- UDP data transmission is more efficient
Question 29: Which of the following is present in a TCP header but not a UDP header?
- Checksum
- Source Port
- Destination Port
- Sequence number
Question 30: Each endpoint of a connection, or socket, contains which of the following pairs of information?
- IP Address and port number
- Sequence number and option type
- MAC address and time-to-live number
- Protocol number and packet ID number
Question 31: Which of the following best describes the Stream Control Transmission Protocol (SCTP)?
- Reliable and message-oriented
- Reliable and character-oriented
- Unreliable and message-oriented
- Unreliable and character-oriented
Question 32: Why does a TCP connection release use a four-way handshake protocol?
- It uses an asymmetric release protocol
- It allows both sides to release independently
- It is the only way to avoid deadlock situations
- It avoids the delays typical to other forms of release
Question 33: A local host has established a TCP connection to a remote host. The local host has 4096 B of data that is ready to send to the remote host. It then receives a segment from the remote host with 2048 B of data and the following parameters in the header: Seq=2048, ACK = 2048, W = 2048. When the local host sends the new segment, which of the following parameters will the header contain?
- Seq = 2048, ACK = 2048, W = 2048, and 2048 B of data
- Seq = 2048, ACK = 4097, W = 2048, and 2048 B of data
- Seq = 4096, ACK = 2048, W = 4096, and 4096 B of data
- Seq = 4096, ACK = 4096, W = 4096, and 4096 B of data
Question 34: IPv6 is more effective than IPv4 due in part to its increased flexibility. Which of the following allows IPv6 to provide more flexibility than IPv4?
- Limited the mix of data streams
- Introduced a fixed-size header with optional extension headers
- Increased the TTL field to allow packets longer travel distances
- Eliminated the support for QoS at an IP level, instead relying on TCP
Question 35: A router receives a packet with a destination IP address of 192.24.10.4 and is using this routing table. What will happen with the packet?
| Address | Mask | Output Port |
| 192.24.0.0 | 255.255.248.0 | 1 |
| 192.24.16.0 | 255.255.240.0 | 2 |
| 192.24.8.0 | 255.255.252.0 | 3 |
| Default | 4 |
- It will be sent to output port 1
- It will be sent to output port 2
- It will be sent to output port 3
- It will be sent to default port 4
Question 36: A school district needs approximately 2,000 IP addresses. A group of addresses starting with 194.24.0.0 is available. You have been assigned the task of giving the school district a number of IP addresses that is as close to 2,000 as possible using CIDR. Which of the following subnets would you assign to the school district to accomplish this?
- 194.24.0.0/16
- 194.24.0.0/21
- 192.24.0.0/24
- 218.238.0.1
Question 37: Which of the following was an early predecessor to the Internet, and arguably where most of the development for today’s internet took place?
- ARPANET
- GOPHER
- LAN
- OSPF
Question 38: Which of the following layers builds on the service provided by the physical layer that lies beneath it?
- Data link layer
- Network layer
- Transport layer
- Physical layer
Question 39: In which of the following situations might you want to consult an RFC?
- To troubleshoot the reason why a router suddenly stops forwarding data
- When your team is designing the network that a community college will use
- To understand how an OSPF router recalculates routes quickly with topology changes
- When you need to choose between two different types of routers for your existing home network
Question 40: A multicast group stops receiving a multicast stream even though there are still members of that multicast group present in the network. Which of the following might be a possible cause for this problem?
- The TTL field became too high
- There was an RPF check failure
- An IGMP Graft message was sent
- The PIM protocol changed from Dense to Sparse
Question 41: A host with an IP address 192.168.10.3/24 needs to send a packet to a remote host with address 192.168.20.40. No default gateway has been configured for the host, but packets are still reaching the remote host. Why might this be the case?
- The host first sends an ICMP Router discovery message
- The gateway responsible for the network is configured as a proxy ARP
- The host issues an ARP request sent to the broadcast Ethernet address
- The sending and destination hosts have both been configured with a mask of 255.255.0.0
Question 42: A channel has a bit rate of 4 kbps and a one-way propagation delay of 20 msec. You are using a stop-and-wait protocol. For what range of frame sizes will you observe at least 50% efficiency?
- 1 to 19 bits
- 20 or more bits
- 80 or more bits
- 160 or more bits
Question 43: 802.16, also known as Wi-Max, has four classes of service. Which of them is the most appropriate to send uncompressed video?
- Best effort
- Constant bit rate
- Real-time variable bit rate
- Non-real-time variable bit rate
Question 44: The Diffie-Hellman algorithm allows hosts to dynamically share secret keys using a public network. Suppose that, before the key exchange, hosts H1 and H2 publicly agree that the values of P is 11 and the value of G is 4. In addition, host H1 has a private secret key of 3, while host H2 has a private secret key of 6. With this information, a “secret” key can be exchanged between hosts H1 and H2. What will the secret key be that is exchanged by H1 and H2 to encrypt and decrypt data as in a symmetric system?
- 4
- 9
- 11
- 64
Question 45: Although cloud computing has many advantages, it is not always the best approach. What would be a typical disadvantage of a cloud computing environment?
- It is harder to maintain
- It typically has slower performance
- It is dependent on devices and their locations
- It can be hard to implement elastically and at scale
Question 46: Which of the following is true about the circuit switching method?
- It is more resilient than other methods in the event of a router failure
- Packets arrive out of order and must be rearranged at the destination
- Each packet has a header with full address of destination and source hosts
- The route from source to destination is determined when a connection is established
Question 47: Which layer of the Internet Protocol describes the protocols for email and web file access?
- Presentation
- Network
- Transport
- Session
Question 48: A user has received an SIP Invite message with this SDP Payload:
CSeq: 1 INVITE
Max–Forwards: 70
Contact: <sip: 9781118484@192.168.215.66:34522>
User–Agent: snom190/3.60s
Allow: INVITE, ACK, CANCEL, BYE, REFER, OPTIONS, NOTIFY, SUBSCRIBE,
PRACK, MESSAGE, INFO
Session–Expires: 3600
Content–Type: application/sdp
Content–Length: 275
v=0
o=root 1747056259 1747056259 IN IP4 192.168.215.66
s=call
c=IN IP4 192.168.215.66
t=0 0
m=audio 49756 RTP/AVP 2 4 0 101
a=rtpmap:2
g726-32/8000
Given this payload, which of the following can we say about this request?
- The call is encrypted with a the key g726-32
- It is for a video call that will take place using port 8000
- It is for an audio call that will take place using port 49756
- The connection uses UDP as its main transport mechanism
Question 49: Which of the following is a difference between SSH and TLS?
- TLS runs on top of UDP, while SSH runs on TCP
- TLS uses a peer-to-peer model, while SSH uses a client-server architecture
- SSH provides for secure data transmission, while TLS provides additional encryption on top of SSH
- SSH provides for secure data transmission, while TLS ensures the integrity and privacy of the message
Question 50: Which of the following characteristics does the User Design Protocol (UDP) have?
- It is connectionless
- It supports user authentication
- It has an unlimited message size
- It is more reliable than other protocols
Question 51: When a router receives a packet, which of the following does it do?
- Check the digital signature
- Translate the network address
- Store the state information about the packet
- Forward the data packets between networks
Question 52: As the network administrator for a medical office, you have decided to put all of the doctors’ machines in subnet 171.157.34.122/28. Which of the following first-available addresses would you need to configure your DHCP server to use for the doctors’ subnet?
- 171.157.34.112
- 171.157.34.113
- 171.157.34.126
- 171.157.34.127
Question 53: Which of the following is a digital cable television system an example of?
- A LAN
- A WAN
- A MAN
- A home networks
Question 54: Which of the following is one of the main differences between RIP and BGP?
- RIP is a TCP-based protocol, while BGP runs directly over IP
- RIP is an exterior routing protocol, while BGP is an interior routing protocol
- RIP is based on distance vector routing, while BGP is based on link state routing
- RIP uses a metric based on hop count, while BGP uses a metric based on path information
Question 55: In which of the following scenarios would you want to enable the RSVP protocol?
- When you want your multicast group to run faster
- When you want to implement a “tagging” protocol operating over UDP
- When you want to implement a “reservation” protocol operating over IP
- When you need a protocol similar to a unicast routing protocol but you are using multicast applications
Question 56: An IPTV system is trying to send high-definition uncompressed video at a resolution of 1600 × 1200-pixel resolution, with 8 bits/pixel, at 60 frames/second. What are the bandwidth requirements for such a system?
- 15.36 Mbps
- 230.4 Mbps
- 115.2 Mbps
- 921.6 Mbps
Question 57: As an experiment, you send a simple IP frame composed of IP header and TCP segment, IPaddr1–TCPsegment, through an IPsec encrypted channel. IPaddr1 is the original IP address on that packet. On the other side of the channel, using a tool like Wireshark to capture and analyze packets, you capture the frame IPaddr2–IPsecHdr–Encryped data. Here, IPAddr2 is the IP header of the captured segment that shows a different, readable IP address. IPsecHdr is the correct and expected readable IPsec header. The rest of the packet is encrypted. What conclusion can you draw from this experiment?
- The system is using IPsec ESP mode
- The system is using IPsec Tunnel Mode
- The system is using IPsec Transport Mode
- The system is experiencing data corruption
Question 58: A VPN connection with a remote server in an office is being rejected. While troubleshooting the issue, you go to the Services Table in the Control Panel and see this partial table:
| Remote Registry | Disabled | |
| RPC Endpoint Mapper | Running | Automatic |
| Routing and Remote Access | Disabled | |
| Secondary Logon | Manual | |
| Sensor Service | Manual | |
| Server | Automatic | |
| Shared PC Account Manager | Disabled |
What is the most likely cause of the problem?
- Remote Registry is disabled
- Secondary Logon is not running
- Routing and Remote Access is disabled
- Shared PC Account Manager is disabled
Question 59: Which layer in the TCP/IP model is a combination of the Application, Presentation, and Session layer in the OSI reference model?
- Application
- Internet
- Network interface
- Transport
Question 60: Which of the following protocols does IGMP normally run on?
- ICMP
- IP
- TCP
- UDP
Question 61: All the client computers on a network are configured to receive IP addresses from a certain DHCP server. However, clients on Subnet B cannot access clients on Subnet A. Which of the following is the most likely cause of this problem?
- IPv6 is disabled
- The server option is disabled
- The IP address is not available in the scope of the DHCP
- The IP address for the DNS Server is not available in the scope option
Question 62: Which of the following outlines three attributes of the HTTP protocol?
- Connection-oriented; port 70, retrieves Hypertext messages from a server
- Connectionless; port 80; retrieves resources like HTML documents from a server
- Menu-driven; port 7070; distributes, searches, and retrieves documents over IP networks
- Peer-to-peer; port 636; establishes secure connections between two machines on a network
Question 63: Your company needs to securely transfer a file between two machines in remote locations. Which of the following would you consider to perform this task?
- Telnet
- Trivial FTP (TFTP)
- Simple FTP (SFTP)
- FTP over SSL (FTPS)
Question 64: While you are holding a chat session with a friend, you can see an indication that your friend is typing. Which of the following describes what the SIP agent on your friend’s machine does as part of this process?
- It sends a SIP INFO packet
- It sends a SIP DIAL message
- It sends an RTCP SDES packet
- It sends an IGMP REPORT message
Question 65: SNMP defines certain aspects of packets that are sent from a manager to an agent. Which of the following is one of those aspects?
- The packet formats
- The packet encoding
- The number of packets
- The username associated with packets
Question 66: Which of the following would be a use case for socket programming?
- When you need to allow two processes within a single machine to communicate
- When you need to allow two processes in two machines on the same network to communicate
- When you need to establish a client/server connection between two computers on the same network
- When you need to create a connection between two processes in different computers or within the same computer
Question 67: Which of the following services does SCTP allow in each association?
- Multistream
- Single-homing
- Congestion control
- Head-of-line blocking
Question 68: A TCP system is very congested. Which of the following is most likely to happen when multiple segments are lost?
- After 4 ACKs are received for the same segment, the sending host reverts to the Slow Start algorithm and starts with a window size of 1
- The sending host will wait for RTO timers to expire and resend lost packets as many times as needed to assure that TCP remains reliable
- After 4 ACKs are received for the same segment, the Fast Retransmit rule is applied and the lost packet is sent without waiting for RTO timers to expire
- After 10 ACKs for the same segment are received, the system automatically switches to the ATM transmission protocol, which is much faster than TCP
Question 69: Which of the following describes one of the differences between a distributed system and a computer network?
- A distributed system does not allow machines to share resources to accomplish a given task, while a network does
- A distributed system requires the use of exterior routing protocols to move data between computers, while a network only uses interior routing protocols
- A distributed system is a collection of autonomous computers operating as one, while a network involves users who each work on individual machines
- In a distributed system all messages have to go through a central node, while a network allows machines to send messages to one another independently
Question 70: Which of the following describes a privately-owned within a campus with machines that spread across a few square miles?
- LAN
- MAN
- WAN
- PAN
Question 71: How does the Link State Algorithm work?
- It floods the network with a link state advertisement at regular intervals
- It exchanges a link state advertisement table with its neighbors at regular intervals
- It uses Dijkstra’s algorithm to find the shortest path between two nodes in the network
- It uses a Poison Reverse algorithm to find the best path between two nodes in the network
Question 72: In an MPLS environment, you see that an LSP is not following the shortest path from source to destination. What should you do in this situation?
- Verify that all routers in the environment are MPLS enabled
- Ignore it, because all links can be used in an MPLS-enabled environment
- Make sure that traffic engineering is correctly guaranteeing the required bandwidth
- Restart the label distribution process which failed to select the best route at startup
Question 73: Why is Address Resolution Protocol (ARP) an important protocol?
- It provides for automatic means of address assignment within a network
- It provides for a convenient way of translating from an IPv4 address to an IPv6 address
- Most hosts are attached to a LAN interface that by definition only understands Ethernet addresses
- Address resolution is required to translate unintelligible IP addresses into familiar, user-friendly names
Question 74: Which of the following is a difference between the Ethernet V2 and 802.3 protocols?
- Ethernet V2 has a maximum frame size of 64KB, while the max frame size of 802.3 is 1500B
- Ethernet V2 uses a CSMA access mechanism, while 802.3 uses a CSMA/CD access mechanism
- Ethernet V2 frame format has a “Type” field, while 802.3 uses a frame format with a MAC subheader
- Ethernet V2 contains the CRC field toward the start of the frame, while 802.3 contains the CRC toward the end of the frame
Question 75: Four computers are connected to an L2 switch and a repeater in a VLAN-unaware network, as shown in this image. PC A attaches to port 1 of the switch and has a MAC address of aa-ab-ac-11-12-13. PC B attaches to port 2 of the switch and has a MAC address of bb-bc-bd-11-12-13. PC C attaches to port 4 of the repeater and has a MAC address of cc-cd-ce-11-12-13. PC D attaches to port 5 of the repeater and has MAC address dd-de-da-11-12-13.

The switch has this Forwarding Database:
Address Port
aa-ab-ac-11-12-13
cc-cd-ce-11-12-13
1
3
PC A sends a frame with a destination MAC address of cc-cd-ce-11-12-13. What will happen with the frame?
- It is received by PC C
- It is received PCs B, C, and D
- It is received by PCs C and D
- It is dropped by the switch, since PC C is not directly connected
Question 76: In this figure, all switches are VLAN-aware, and have a native VLAN ID for each port as shown. In addition, each port has been statically configured to the indicated VLANs. The link between SW1 Port 2 and SW2 Port 3 is 802.1Q, and is a trunk. The link between SW1 Port 6 and SW3 Port 7 is not a trunk. The MAC rectangles represent hosts with the indicated MAC address. These MAC addresses have been abbreviated for convenience. Consider the FDB on all switches to be empty at the beginning of the situation presented.
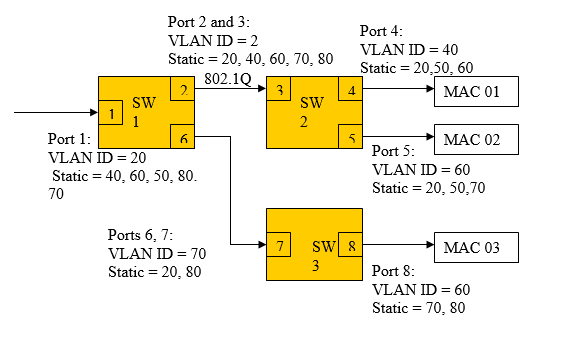
In this situation, a “clear” frame (with no VLAN ID) comes into port 1 of SW1 with a destination of MAC 01. What will happen with the frame?
- It will be dropped by SW1
- It will reach both SW2 and SW3, but both will drop it
- It will reach both SW2 and SW3, but go out of port 8 on SW3
- It will reach both SW2 and SW3, but go out of ports 4 and 5 on SW2
Question 77: What is the difference between the token ring and token bus protocols?
- Token ring is an actual ring with a circulating token, while token bus is a virtual ring where the token circulates on a bus
- Token ring uses a transmission timer to transmit once it gets the token, while token bus transmits as soon as the token is available
- Hosts with data in a token ring must wait for the token to arrive before transmission, while hosts with data in a token bus can transmit at any time
- A host in a token ring does not monitor the media since access is based only on having the token available, while a host in token bus monitors the media before sending data
Question 78: Encrypting a message is not useful if you can’t verify that the message gets to the correct recipient. Typically, digital signatures are used to solve this problem. How are digital signatures created?
- By exchanging the roles of the Authentication field (AH) and the Encapsulating Security Header (ESP) field in the IPsec header
- By using a tunnel-mode algorithm where the sender encrypts a signature and sends it through a tunnel previously made with the receiver
- By the sender encrypting a signature using a private key and the receiver using a public key to decrypt the signature to verify authenticity of the sender
- By the sender encrypting a signature using a private key and the receiver using the same private key to decrypt the signature to verify authenticity of sender
Question 79: Your attempt to establish an RDP connection to a remote computer keeps failing. You have verified that you have appropriate admin credentials, and that the remote computer is configured to allow users to connect remotely. Which of the following could be a cause of this issue?
- Another program is using port 3389
- IKE services are disabled on the remote system
- Shared PC Account Manager is disabled in the remote system
- There is a mismatch in the Security Associations for the connection
Question 80: Two common cloud computing platforms are Amazon’s AWS and Microsoft’s Azure. What is one of the main differences between the two?
- AWS uses SQL databases like MYSQL, while Azure uses a relational database like RDS
- AWS is based on Elastic Compute Cloud (EC2), while Azure is based on virtual machines
- AWS uses the more efficient block storage, while Azure uses object storage through a web interface
- AWS uses a network platform based on virtual networks, while Azure is based on a virtual private cloud
Question 81: Which of the following is true about the datagram method of packet switching?
- Each packet’s path is chosen randomly between a limited set of paths
- Each packet has a header with full address of destination and source hosts
- A path must be established from source to destination before data starts flowing
- Even though a path is not established ahead of time, each packet must follow the exact same path
Question 82: Which of the following statements about packets in a reliable connectionless service is true?
- They cannot be lost
- They can be modified
- They can be duplicated
- They can suffer transmission errors
Question 83: This is a segment of a DNS database for cs.upr.pr.
cs.upr.pr.
cs.upr.pr.
86400
86000
IN
IN
TXT
MX
free access
1 correo.cs.uprm.pr
rapi.cs.upr.pr.
rapi.cs.upr.pr.
rapi.cs.upr.pr.
www.uprm.pr.
86000 IN
86000 IN
86400
86400
HINFO
A
IN
IN
A
CNAME
RedHat Unix
129.105.77.32
192.162.209.44
colegio.cs. uprc
Tiger
Tarazan
Printer
IN
IN
IN
IN
IN
IN
IN
IN
A
HINFO
MX
A
HINFO
MX
A
HINFO
129.105.80.101
RedHat Unix
1 correro
129.105.50.44
Sun Unix
1 Correro
192.162.50.144
Laserjet
According to the table, what network class is Tarzan on?
- Class A
- Class B
- Class C
- Class D
Question 84: Which of the following fields in the TCP headers is used for flow control?
- Window size
- Urgent pointer
- TCP checksum
- Destination port
Question 85: Each end of the TCP connection uses a buffer to speed up data flow when the network is busy. Which of the following processes manages the flow controls?
- Buffer control
- Sliding window
- Traffic avoidance
- Congestion control
Question 86: You have determined that the round-trip time for a connection in your network is 10 ms. You are making a new TCP connection using Slow Start. The receive window is 24KB and the maximum segment size is 2KB. How long would you expect to take before the first full window of 24KB is sent?
- 10 ms
- 20 ms
- 30 ms
- 40 ms
Question 87: How does the Distance Vector algorithm work?
- It floods the network with a distance vector table at regular intervals
- It exchanges a distance vector table with its neighbors at regular intervals
- It uses Dijkstra’s algorithm to find the shortest path between two nodes in the network
- It uses a count-to-infinity algorithm to find the best path between two nodes in the network
Question 88: After the only member of a multicast group leaves the group, the multicast stream continues to flow for exactly 3 additional minutes before going silent. Which of the following is the most likely cause for this?
- The router is running IGMP version 1, which is outdated
- There is a failing DVMRP router that times out in exactly 3 minutes
- The router is sending the leave request to the wrong multicast address, 224.0.0.2
- The Protocol Independent Multicast (PIM) enabled router times out in exactly 3 minutes
Question 89: You are sending a ping command via ICMP to a remote address, but you receive a “Destination Unreachable” message with a code of 4 in the header. Which of the following might be a reason for this?
- The packets are looping endlessly
- The datagram is too big and the DF bit is set
- An illegal value has been detected in a header field
- The router has noticed that a packet seems to be routed incorrectly
Question 90: The string 0111101111101111110 needs to be transmitted via the data link layer. After bit stuffing, what would the transmitted string actually look like?
- 011110111101011110110
- 011110111110011111010
- 001111001111100111111100
- 0111110011111010111110100
Question 91: CSMA is a protocol that does which of the following?
- Determine who accesses the media in a multi-host environment
- Route L2 traffic from source to destination based on the state of the media
- Monitor transmission media to determine when it is congestion and alert users
- Retransmit a damaged packet based on a random timer that is started when a collision occurs
Question 92: Which of the following statements is true?
- TCP is a connection-oriented service, which means that connections are very reliable
- TCP is a connectionless service, which means that segments are always accounted for
- In a connection-oriented service like UDP, lost segments are accounted for, but not retransmitted
- In a connectionless service like UDP, all segments are always acknowledged and lost ones retransmitted
Question 93: Which of the following services is provided by the physical layer?
- User authorization
- Transmission of long messages
- Transfer of data frames from one node to another
- Mechanical and electrical properties of transmission media
Question 94: Which of the following is one of the main differences between the IMAP and POP protocols?
- IMAP is used to retrieve emails from a server, while POP is used to send emails
- POP is used to retrieve emails from the server, while IMAP is used to send emails
- IMAP messages are stored in a mail server, while in POP messages are downloaded to the local machine
- POP messages are accessible from any machine anywhere, while IMAP can only retrieve emails from the local machine
Question 95: Which of the following SNMP processes does a manager run?
- Client
- Server
- TCP
- UDP
 Clear My Certification All Certification Exam Answers
Clear My Certification All Certification Exam Answers



